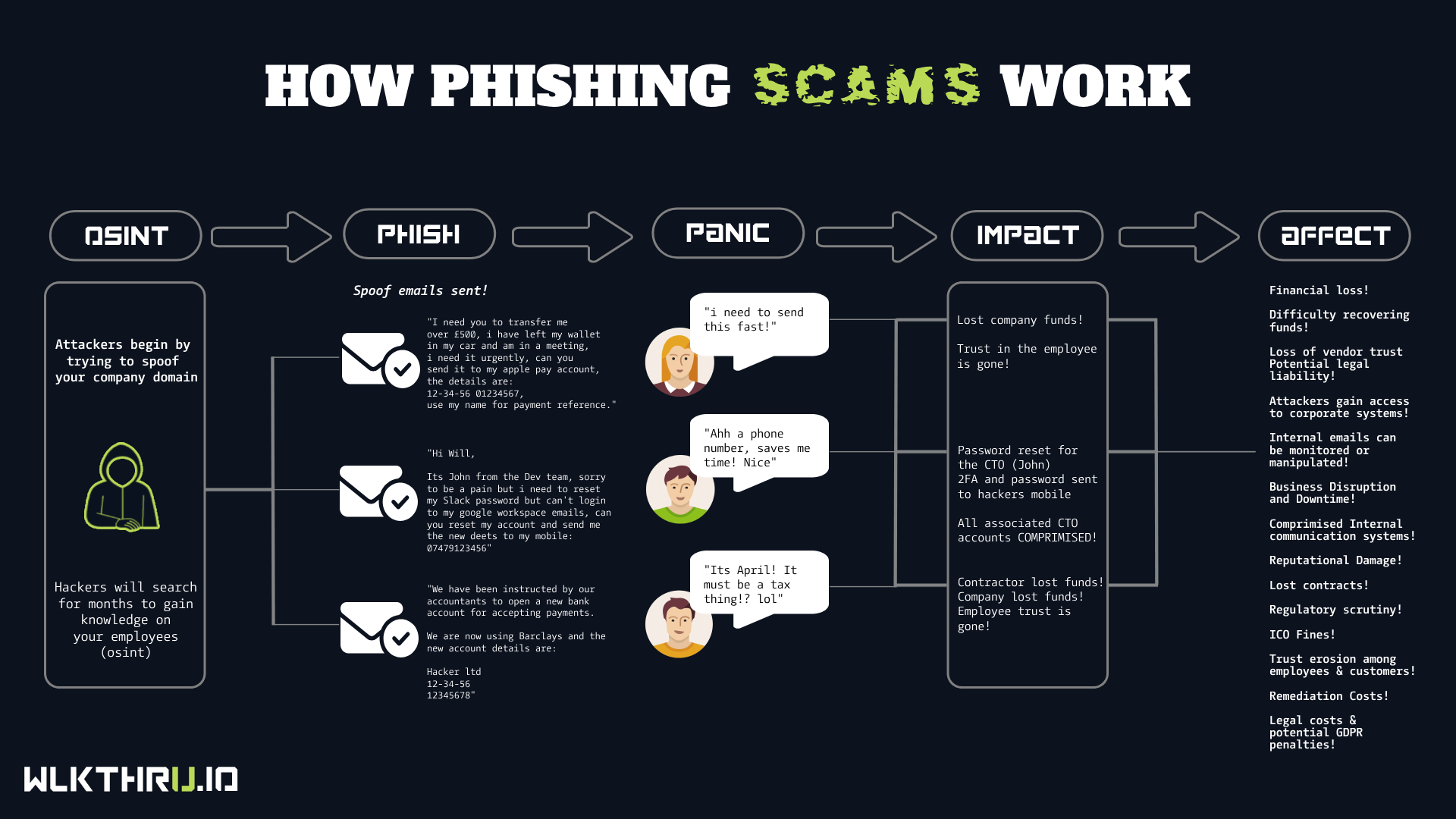
In today's digital age, cyber threats are more sophisticated than ever, and no business is immune. This is the story of a UK-based company that fell victim to a meticulously crafted phishing scam, resulting in a £120,000 loss and significant operational disruption.The Incident: A Deceptive Email Leads to CatastropheAn employee received an email that appeared to be from the company's CEO, requesting an urgent payment to a new supplier. The email was convincing, complete with the CEO's signature and writing style. Trusting the request, the employee transferred £120,000 to the specified offshore account.Simultaneously, the attackers exploited the breach to reset the company's Microsoft 365 admin credentials. This action locked the entire organization out of their email and OneDrive accounts for several days, halting communications and access to critical documents.The Aftermath: Financial and Reputational DamageThe immediate financial loss was substantial, but the repercussions extended further: Operational Disruption: The inability to access email and documents crippled daily operations. Client Trust Erosion: Clients, unable to communicate with the company, began to question its reliability. Employee Morale: The incident led to internal investigations and strained employee relations. Layoffs: The financial strain forced the company to make difficult staffing decisions. Understanding the Attack: Business Email Compromise (BEC) This incident is a classic example of Business Email Compromise (BEC), where attackers impersonate company executives to trick employees into transferring funds or revealing sensitive information. According to the FBI, BEC scams have cost businesses worldwide approximately £9.52 billion over the past five years . Prevention Strategies: Safeguarding Your Business To protect against such threats, businesses should implement the following measures: Employee Training: Regularly educate staff about phishing tactics and how to recognize suspicious emails. Verification Protocols: Establish procedures for verifying financial requests, such as dual-approval systems or direct confirmation with the requester. Multi-Factor Authentication (MFA): Implement MFA across all accounts to add an extra layer of security. Regular Audits: Conduct periodic security audits to identify and address vulnerabilities. Incident Response Plan: Develop and maintain a clear plan for responding to security breaches.Conclusion: Vigilance is Key This unfortunate event serves as a stark reminder of the importance of cybersecurity. By understanding the tactics used by cybercriminals and implementing robust security measures, businesses can better protect themselves from similar attacks. Stay informed, stay prepared, and prioritize cybersecurity to safeguard your organization's future. In April 2022, a Lancashire-based business experienced a significant financial loss due to a sophisticated phishing scam. An employee, deceived by a fraudulent email, entered their Microsoft 365 login credentials into a counterfeit site. This breach allowed cybercriminals to access the company's email system, leading to a series of deceptive communications that culminated in a £12,400 payment to an imposter posing as a trusted supplier. The Anatomy of the AttackInitial Breach The attack began with a phishing email that directed an employee to a fake Microsoft 365 login page. Believing it to be legitimate, the employee entered their credentials, granting the attacker access to the company's email system. Exploitation of Trust With access to internal communications, the attacker identified a longstanding supplier relationship. They then created a spoofed email domain closely resembling the supplier's and initiated a conversation about an outstanding payment. Over several days, the attacker engaged in persuasive communication, eventually convincing the company to transfer £12,400 to a fraudulent account. The Aftermath The financial loss was immediate, but the repercussions extended further. The breach exposed vulnerabilities in the company's cybersecurity measures, particularly the lack of multi-factor authentication and employee training on phishing threats. In response, the company implemented stronger security protocols, including mandatory multi-factor authentication and enhanced employee awareness programs. Lessons LearnedEmployee Training: Regular training sessions can equip employees with the knowledge to identify and report phishing attempts.Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, making it more difficult for attackers to gain unauthorized access.Email Verification Protocols: Establishing procedures to verify changes in payment details can prevent fraudulent transactions.Regular Security Audits: Periodic reviews of security measures can identify and address potential vulnerabilities.ConclusionThis incident underscores the importance of robust cybersecurity practices. By understanding the tactics used by cybercriminals and implementing comprehensive security measures, businesses can protect themselves from similar threats. Proactive steps, such as employee training and multi-factor authentication, are essential components of a strong cybersecurity strategy.