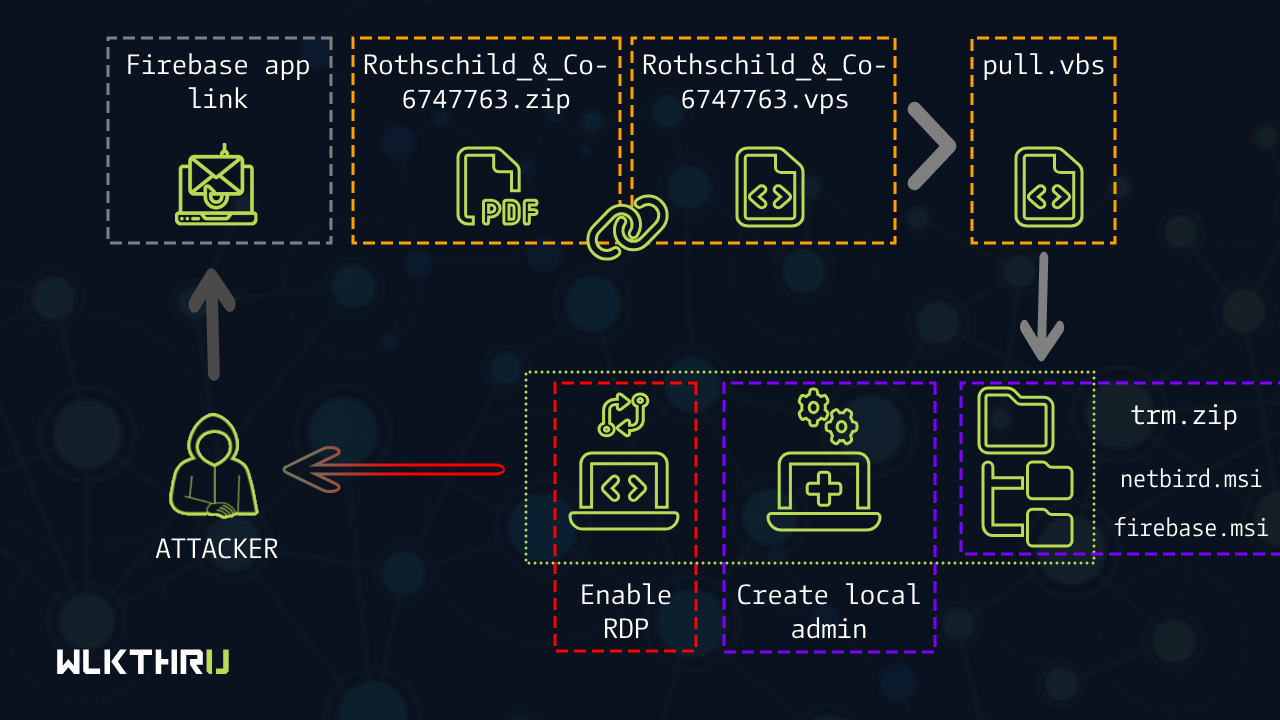
A recent high-profile spear-phishing campaign has shed light on how even legitimate open-source tools like NetBird can be twisted for malicious purposes. Aimed squarely at CFOs and senior finance personnel across global industries, including banking, energy, and insurance, the attack chain cleverly bypassed traditional defenses and leveraged custom CAPTCHA evasion, remote administration tools, and hidden user accounts. Let’s break it down, step-by-step, so you and your team can recognize and defend against similar threats.What Happened? On May 15th, Trellix’s email security tools flagged a coordinated spear-phishing attack targeting financial leaders in Europe, Africa, the Middle East, Canada, and South Asia. The attackers’ endgame? Deploying NetBird, a legitimate WireGuard-based networking tool, to gain covert access through encrypted tunnels and persistent local administrator accounts. It’s worth noting: there’s no vulnerability in NetBird itself.This was about weaponising its capabilities through stealthy misuse, not exploiting code flaws.The Attack Flow: From Inbox to BackdoorStep 1: The Bait Victims received highly personalized emails posing as job offers from Rothschild & Co.Attached was a so-called “brochure” that, instead of being a PDF, linked to a Firebase-hosted phishing page.Subject line: “Rothschild & Co leadership opportunity (Confidential)”Link destination: A custom CAPTCHA puzzle hosted at firebaseapp[.]com Step 2: CAPTCHA Evasion & ZIP DeliveryTo pass the CAPTCHA, victims had to solve a math puzzle that decrypted a hidden URL.That redirected them to a second Firebase page which served a ZIP file named:Rothschild_&_Co-6745763.zipInside was a 1KB .vbs script a deceptively small file that launched the attack.Step 3: VBS DownloaderThe first VBS file:Created a hidden C:\temper\ directoryDownloaded a payload from:http://192[.]3[.]95[.]152/cloudshare/atr/pull.pdfSaved it as pull.vbs and executed it via wscript.exe with admin privilegesStep 4: Stage-Two – NetBird DeploymentThe pull.vbs script:Downloaded trm (renamed trm.zip) Extracted NetBird and OpenSSH MSI installersInstalled both silently, started services, and activated NetBird using a pre-defined key Created a local admin account named user with RDP enabled and firewall exceptionsScheduled a NetBird startup task on every boot.The Bigger Picture This isn’t just a one-off. The attackers reused infrastructure from older phishing domains (also CAPTCHA-protected), and even impersonated France’s AMF regulator in some variants.Why It Matters (and What to Do About It) This campaign is a masterclass in social engineering and defense evasion.Legitimate-looking emails, encrypted phishing pages, script-based execution, and low-noise persistence techniques all combine to evade most default enterprise defenses.For Leaders and Employees:Never open ZIP attachments from unknown senders, especially with recruitment luresReport any odd recruiter emails to your security teamDon’t ignore browser or email security warningsFor Cybersecurity Teams:Watch for: wscript.exe/powershell.exe activity from executive accounts.Monitor for local admin account creation, especially generic usernames like "user"Set alerts on suspicious MSI installations and ZIP + VBS combosIntegrate phishing simulations that reflect this level of sophistication wlkthru Key TakeawaysThis attack is a case study in modern phishing sophistication, one that fits perfectly into our training curriculum.We recommend all Team and Company subscribers run a simulated attack based on this case to reinforce awareness and response procedures.We’re also updating our “Secure Email Handling” module this month to include walkthroughs of this campaign.Indicators of Compromise (IOCs) What to look out for:Sender Address(Spoofed Rothschild recruiter): <redacted>@notarius.netReply-To Email(Mismatched reply field):db2680688@gmail.comIP (C2)(Hosted payloads): 192.3.95.152ZIP Filename(Contains initial VBS dropper): Rothschild_&_Co-6745763.zipVBS Hash(Stage-1 downloader): 53192b6ba65a6abd44f167b3a8d0e52dPayload URL(NetBird MSI): http://192.3.95.152/cloudshare/atr/trmFake Admin(Created for persistent access): user / Bs@202122 Stay sharp, stay safe. For a walkthrough simulation of this attack and guided incident response training, visit your Team Dashboard on wlkthru.io.